Understanding Firewalls
Introduction
**Cyber Threat Alert!** Every **39 seconds**, a cyberattack occurs worldwide, targeting both individuals and businesses. Without a proper security system, your personal data, financial information, and even your identity can be at risk.
Imagine you're the **owner of a house**. Would you leave your **doors and windows unlocked**, allowing strangers to walk in freely? Of course not! The same principle applies to your digital devices. **Firewalls act as security guards**, monitoring who enters and exits your network, blocking malicious threats before they cause harm.
With **remote work, online banking, and digital transactions** becoming the norm, cybercriminals have more opportunities than ever to exploit vulnerabilities. **Firewalls are essential** in safeguarding not just big enterprises but also personal devices and home networks.
In this guide, we'll dive deep into:
- **What is a Firewall & How Does It Work?**
- **Types of Firewalls & Their Role in Cybersecurity**
- **How Firewalls Protect You from Hackers & Malware**
**By the end of this blog**, you'll have a clear understanding of why firewalls are a **must-have** security tool in today's digital landscape.
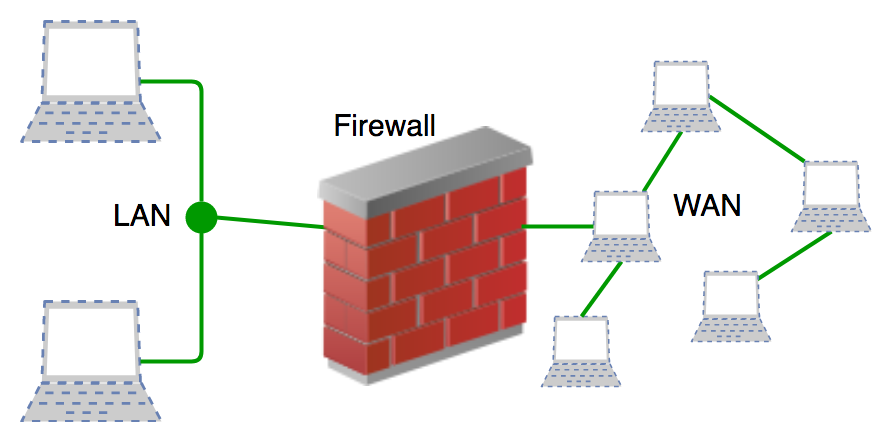
What is a Firewall?
A **firewall** is a **security system** that acts as a **barrier** between your trusted network (like your home or office) and external networks (such as the internet). It **monitors, filters, and controls** incoming and outgoing network traffic based on predefined security rules.
**Think of a firewall like a security guard at the entrance of a building.** It decides who is allowed in and who should be denied entry, ensuring only trusted individuals can pass through while keeping out potential threats.
How Does a Firewall Work?
Firewalls **examine data packets** that travel in and out of your network. These packets contain information about their origin, destination, and type of data they carry.
The firewall **analyzes each packet** based on a set of **security rules** to determine if it should be allowed or blocked.
If a packet appears **suspicious or malicious**, the firewall **blocks it immediately**, preventing cyber threats like hacking, malware, or unauthorized access.
Firewall Process Flow
- Step 1: Data packets try to enter or exit your network.
- Step 2: The firewall inspects the packet for security threats.
- Step 3: If the packet follows security rules, it is allowed through.
- Step 4: If the packet is suspicious, it is blocked and logged.
Why Are Firewalls Important?
Firewalls are **crucial** in **cybersecurity** because they:
- Block Malware – Prevent viruses, spyware, and ransomware attacks.
- Stop Unauthorized Access – Prevent hackers from infiltrating networks.
- Secure Online Browsing – Filter harmful websites and phishing attempts.
- Protect Organizations – Secure company networks from external threats.
Types of Firewalls
Firewalls come in different types, each designed for specific security needs. Below are the **most common types of firewalls** and how they function.
1. Packet Filtering Firewall
A **packet filtering firewall** inspects individual packets of data based on **IP addresses, ports, and protocols** before allowing or blocking them.
**Example Use:** Used in small office networks to block unauthorized traffic.
2. Stateful Inspection Firewall
This firewall **monitors active connections** and inspects packets based on both the **current state of the connection and security rules.**
**Example Use:** Found in enterprise networks for advanced security filtering.
3. Proxy Firewall
A **proxy firewall** acts as an **intermediary** between users and the internet, filtering traffic and hiding internal network details.
**Example Use:** Used in **organizations and schools** to block access to malicious or restricted websites.
4. Next-Generation Firewall (NGFW)
NGFWs combine **traditional firewall features** with **intrusion prevention systems (IPS), deep packet inspection, and advanced threat detection.**
**Example Use:** Used in **large enterprises** for high-level network security and advanced monitoring.
5. Cloud-Based Firewall
A **cloud firewall** provides security at the cloud level, filtering traffic before it reaches a company’s internal network.
**Example Use:** Used by **businesses with cloud infrastructure** for scalable protection.
6. Web Application Firewall (WAF)
WAFs protect **web applications** by filtering and monitoring **HTTP/HTTPS traffic** to prevent attacks like SQL injection and cross-site scripting (XSS).
**Example Use:** Used by **e-commerce websites** to prevent hacking attempts.
How Firewalls Protect Against Cyber Threats
Firewalls play a **vital role** in protecting networks from various cyber threats. They act as the **first line of defense** by monitoring and filtering incoming and outgoing traffic.
1. Blocking Unauthorized Access
Firewalls prevent **unauthorized users** from accessing sensitive data by **restricting traffic** based on security policies.
**Example Use:** A company’s firewall **blocks hackers** from accessing internal employee databases.
2. Preventing Malware and Viruses
Firewalls scan **incoming files and data packets** to detect and block potential **viruses, trojans, and ransomware**.
**Example Use:** A firewall **blocks malicious email attachments** that contain viruses before they reach employees.
3. Stopping DDoS Attacks
Firewalls detect **unusual traffic spikes** and block **Distributed Denial-of-Service (DDoS) attacks**, which overwhelm networks with excessive requests.
**Example Use:** A cloud-based firewall **prevents a DDoS attack** from shutting down an e-commerce website.
4. Protecting Against Phishing Attacks
Firewalls **analyze web traffic** and block access to **malicious websites** that attempt to steal user credentials.
**Example Use:** A firewall **blocks fake banking websites** that trick users into entering login details.
5. Monitoring Network Traffic
Firewalls continuously **analyze network traffic patterns**, helping security teams detect **suspicious activity** and potential breaches.
**Example Use:** A firewall **alerts administrators** when an unusual login attempt is detected from an unknown location.
6. Preventing Data Leaks
Firewalls help prevent **unauthorized data transfers** by blocking sensitive files from being sent outside the organization.
**Example Use:** A company firewall **stops confidential employee records** from being shared over email without permission.
Benefits of Using Firewalls
Firewalls are essential for **network security**, offering multiple benefits that keep **organizations, businesses, and individuals safe** from cyber threats.
Enhanced Security
Firewalls act as a **protective barrier**, blocking unauthorized access and preventing cyber threats from infiltrating networks.
**Example Use:** A company's firewall **blocks hackers** from accessing internal databases containing sensitive employee information.
Protection Against Hackers
Firewalls prevent **unauthorized users** from remotely controlling your system or stealing personal data.
**Example Use:** A firewall **blocks brute-force attacks** attempting to guess a user's password.
Safe Browsing Experience
Firewalls **filter malicious websites**, protecting users from phishing scams and fake links.
**Example Use:** A school firewall **blocks students from accessing harmful or illegal websites.**
Protection Against Malware
Firewalls detect and **block malware** before it can infect a system or spread across a network.
**Example Use:** A business firewall **blocks an infected email attachment** from delivering ransomware.
Network Traffic Monitoring
Firewalls provide **real-time monitoring**, analyzing data packets to detect suspicious activity.
**Example Use:** A firewall **detects and reports abnormal spikes in traffic**, preventing data breaches.
Prevention of Data Leaks
Firewalls stop **unauthorized data transfers**, ensuring sensitive information is not leaked or shared.
**Example Use:** A government firewall **prevents employees from sharing classified documents** outside the network.
Better Performance and Efficiency
Firewalls help **optimize network performance** by filtering unnecessary traffic and reducing system load.
**Example Use:** A firewall **blocks unnecessary background processes**, improving internet speed.
Conclusion
Firewalls play a **crucial role in cybersecurity**, acting as the first line of defense against online threats. Whether for individuals, businesses, or enterprises, implementing a strong firewall ensures **better security, privacy, and network stability**.
Understanding how firewalls work and the different types available helps you **choose the right protection** for your needs. Regular updates, proper configurations, and combining firewalls with other security measures will significantly **enhance your cybersecurity posture**.
Cyber threats are constantly evolving, and so should your knowledge! Stay informed, keep your systems updated, and spread awareness about the importance of firewalls. A safer internet starts with **you**.
Looking to boost your cybersecurity knowledge? Check out platforms like TryHackMe and Cybrary.